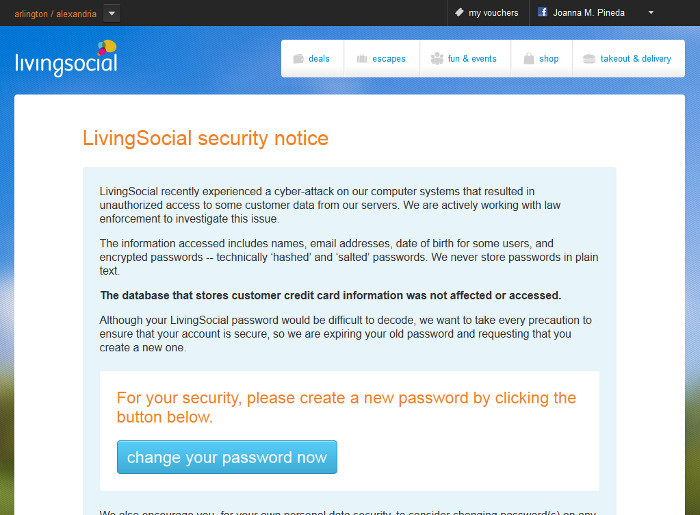
A couple of weeks ago, the daily deal website LivingSocial reported a cyberattack that breached the accounts of some 50 million subscribers. The information breached included names, email addresses, date of birth, and encrypted passwords. Ugh. These system breaches are so common these days that we change passwords, shrug and move on. And yet most people aren’t learning the real lessons of password management.
I spoke at a conference recently where I asked the audience how many of them use the same passwords on multiple sites. About half the hands went up. I get it, it’s impossible to remember a different password for every site that requires one, but most people don’t realize is how one system breach makes you vulnerable to others, even if the other systems are not breached. Here’s how it works: Say you bought something from a retailer and you used the same username and password that you use on other sites. The retailer’s system is breached. You change your password and you’re done, right? Wrong. The hackers take the breached usernames and passwords and try them against major retailer and social networking sites because, let’s face it, who doesn’t have an Amazon, Google, Facebook, Twitter, Ebay, iTunes, Fidelity or Schwab account? For the person who used the same password on multiple systems, he just got ripped off across multiple platforms. Total disaster.
Want to protect your information and assets? Here are some guidelines.
Use one password per site. That’s right. Use a different password for Amazon, Google, iTunes, Facebook, eTrade, your child’s school website, The Washington Post, LivingSocial, Etsy, and on and on. This way, if one system is breached and the hackers manage to unencrypt your account information, they can’t use it on other sites.
Use a secure password manager. It’s going to do you no good to have dozens of different passwords if you don’t have a good system for managing them. I have a friend who says she has an Excel file on her computer that contains her passwords. Trust me, if you computer got lost, stolen or otherwise breached, that Excel file is toast. The net admins at Matrix Group like KeePass and LastPass. I use KeePass to store all of my passwords. I have one, really strong password to my KeePass account that I have committed to memory; KeePass handles everything else. Okay, that’s not exactly true. I’m paranoid enough that the passwords to my email, laptop and work network are committed to memory, never written down and not stored in KeePass.
Use really strong passwords. A really strong password is long, contains a combination of letters, numbers and characters, and has an element of randomness to it. I really like this article by Thomas Baekdal on the Usability of Passwords. He argues that users should create long, memorable passwords that combine words and characters. If a password is memorable, you’re more likely to remember it and you won’t write it down on a Post It note. An example would be: 99BlueBellagioBalls. This password is easy to remember but it’s long, it’s got upper and lower case letters and it’s got numbers. A more recent article by Dan Goodin (Why passwords have never been weaker — and crackers have never been stronger in) says the hacking landscape has changed dramatically because of supercomputers and password breaches that have exposed common passwords and password patterns that people use over and over again. The solution? Use an even longer, complex password: 99BlueBellagioBalls might become Blue99beLLagioBalls. This is a 19-character password that you could more easily remember than 98zefswr))*je. But then again, if you’re using a password manager, you won’t need to memorize your long passwords.
If a system allows two-factor authentication, opt for it. Two factor authentication means you need two factors to get in. To access Facebook from a new computer, you would need your username and password AND the code that Facebook sends to your phone. Presumably, a hacker would not have access to your phone.
Don’t use weak security questions. Personally, I’m appalled that a woman’s maiden name is still used as a security question. Since I didn’t change my last name when I got married, the whole world knows my maiden name. The lesson here is this: don’t select a security question where the answer can be easily obtained by a casual acquaintance, doing Google searches or checking out your profile on Facebook.
I guess I could decide to live in a treehouse, go off the grid and use only cash but who am I kidding? There are myriad government and corporate systems that have information on me and those systems can be breached. The best I can do is protect my accounts with strong passwords that I manage securely. I hope you all will do the same.

One reply on “Time To Get Serious About Your Passwords”
Totally agree about the lame security questions! Especially mother’s maiden name. Not only does it assume that women change their names when they marry, but that somehow their former names are so disconnected from them that knowledge of that name is somehow secure. It’s absurd.
If you DO decide to go live in a treehouse, can I come visit? (also, read this book: http://www.amazon.com/Miss-Twiggleys-Tree-Dorothea-Warren/dp/1930900171)